Services
What we do
Elevate Your Business with Managed IT Services
Managed IT Services
24/7 support, 99% uptime guarantee, and cutting-edge cybersecurity. Explore cloud solutions, offsite backup, and tailored business strategies.
24/7 365 Services
Experience uninterrupted support with our round-the-clock, 365 days a year service. We understand that technology doesn't take breaks, and neither do we.
Monitoring: Uptime Warranty 99%
Ensure the reliability of your systems with our proactive monitoring services. We guarantee a 99% uptime, providing you with the peace of mind that your business operations are running smoothly.
Offsite Backup
Protect your valuable data with our offsite backup solutions. Safeguard against unforeseen events and data loss, ensuring that your critical information is always secure and retrievable.
Cloud Solutions
Harness the power of the cloud to enhance your business efficiency. Our tailored cloud solutions offer scalability, flexibility, and accessibility, allowing you to focus on your core operations.
Cybersecurity
Stay ahead of cyber threats with our robust cybersecurity measures. We prioritize the security of your digital assets, implementing cutting-edge solutions to safeguard your business from potential risks.
Business Solutions
Our comprehensive business solutions go beyond IT support. We work closely with you to understand your unique needs, offering tailored strategies and technologies to drive your business forward.
Empower Your Business with Cutting-edge Cloud Technology
Cloud Solutions
Unlock the potential of Cloud Solutions to streamline your operations, enhance collaboration, and ensure data security.

Private Hosting
For the utmost control and security, opt for our private hosting solutions. Tailored to your specific requirements, our private hosting services provide a dedicated environment, ensuring the confidentiality and integrity of your data.
Harness the power of Cloud Solutions to propel your business forward. Embrace efficiency, security, and scalability like never before.
Cloud Storage
Effortlessly store and access your data from anywhere with our secure cloud storage solutions. Enjoy scalable storage options that adapt to your business needs, providing flexibility without compromising on security.
Cloud Backup
Protect your critical data with our reliable cloud backup services. Ensure business continuity with automated, secure, and easily recoverable backup solutions. Your data's safety is our priority.
Cloud Hosting
Experience superior performance and scalability with our cloud hosting services. From web applications to databases, our cloud hosting ensures optimal efficiency, allowing your business to thrive in the digital landscape.
Safeguarding Your Digital Landscape with Robust Security Solutions
Network Security
Explore our comprehensive network security services designed to fortify your business against evolving cyber threats.
Elevate your network security with our comprehensive suite of solutions. Trust us to safeguard your digital assets, allowing you to focus on what matters most – the growth and success of your business.

Cybersecurity
Our cutting-edge cybersecurity measures go beyond the conventional, ensuring that your digital assets are shielded against the latest threats. Stay ahead in the cybersecurity landscape with our proactive approach.
VPN (Virtual Private Network)
Securely connect your remote teams and protect sensitive data with our VPN solutions. Enjoy a private and encrypted connection, fostering a seamless and secure work environment.
Monitoring
Proactive monitoring is the key to a secure network. Benefit from real-time insights into your network’s health and potential vulnerabilities, allowing us to address issues before they become threats.
Backup & Recovery
Safeguard your data with our robust backup and recovery solutions. Ensure business continuity and rapid recovery in the face of data loss or cyber-attacks, minimizing downtime and preserving critical information.

Training
Empower your workforce with cybersecurity awareness training. Equip your team with the knowledge to identify and thwart potential threats, turning them into the first line of defense against cyber-attacks.
Disaster Recovery
Prepare for the unexpected with our disaster recovery services. Minimize downtime and data loss in the event of a disaster, ensuring that your business can swiftly recover and resume operations.
SOCII
Trust in our SOCII compliant practices, emphasizing the security, availability, processing integrity, confidentiality, and privacy of your data. Rest easy knowing that your information is handled with the utmost care.
Penetration Testing
Identify and address vulnerabilities with our penetration testing services. Proactively assess your network’s security posture and take strategic steps to enhance your defenses against potential cyber threats.

Firewall Protection
Secure your network perimeter with our firewall protection solutions. Customize and implement robust firewalls to monitor and control incoming and outgoing network traffic, preventing unauthorized access.
Anti-Virus
Stay protected against malware, ransomware, and other cyber threats with our advanced antivirus solutions. Our proactive approach ensures that your systems are fortified against evolving threats.
2FA and MFA
Enhance user authentication with our 2FA and MFA solutions. Add an extra layer of security to your network, ensuring that only authorized individuals can access critical systems and data.
Tailored Solutions for Your Unique Business Needs
Business Solutions
At 1TEC, we understand that every business is unique. That’s why our approach begins with a thorough analysis of your workflow and needs, allowing us to recommend customized solutions that drive efficiency and growth.
Discover the power of tailored business solutions that align with your unique requirements. Let 1TEC be your strategic partner in driving productivity, efficiency, and success.
Analyzing Your Workflow and Needs
Before we propose any solution, we delve deep into understanding your business processes. Our team conducts a comprehensive analysis, mapping out your workflow and identifying key pain points. This meticulous approach ensures that the solutions we recommend align seamlessly with your business objectives.
VoIP
Transform your communication infrastructure with our VoIP solutions. Enjoy cost-effective and efficient communication, whether it’s within your organization or with clients and partners.
ERP & CRM
Streamline your business operations with our ERP/CRM solutions. From managing resources to enhancing customer relationships, our integrated systems provide a centralized platform to optimize your processes.
Data Workflow Optimization
Optimize the flow of data within your organization. Our solutions focus on efficient data handling, reducing bottlenecks, and ensuring smooth information exchange across departments.
Digital Signage
Capture attention and convey messages effectively with our digital signage solutions. From promotional displays to internal communication, our solutions are designed to leave a lasting impression. Digital Signage FAQ
Documentation Solutions
Organize and streamline your documentation processes. Our solutions cater to both internal and customer-facing documentation, ensuring clarity, accessibility, and compliance.
Conference Room Solutions
Facilitate seamless collaboration with our conference room solutions. Whether in-person or virtual, our technologies ensure that your meetings are productive and efficient.
Increase Productivity
Empower your team with solutions that boost productivity. From collaborative tools to workflow automation, we identify and implement strategies to enhance efficiency across your organization.
Private Data: Backup and Recovery
Safeguard your critical business data with our private backup and recovery solutions. Minimize downtime and ensure that your data is secure, allowing you to focus on your core business activities.
Elevate Your Business with Microsoft's Powerful Suite
Microsoft Solutions
Explore a range of Microsoft solutions designed to enhance collaboration, productivity, and security for your business.
Discover the versatility of Microsoft solutions tailored to meet the specific needs of your business. From cloud collaboration to identity management, we provide a seamless integration of Microsoft technologies that drive efficiency and success.
Office 365
Transform the way your team collaborates with Office 365. Harness the power of familiar tools like Word, Excel, and PowerPoint, now with cloud-based collaboration features that bring efficiency to your daily tasks.
OneDrive
Empower your workforce with secure and accessible cloud storage. OneDrive ensures that your files are readily available, facilitating seamless collaboration while maintaining robust security measures.
SharePoint
Optimize team collaboration and information sharing with SharePoint. Create, manage, and share content and applications, fostering a collaborative environment that enhances productivity across your organization.
Azure Active Directory
Securely manage and authenticate user access with Azure AD. Benefit from a comprehensive identity and access management solution that integrates seamlessly with Microsoft 365 and other cloud applications.
Local Active Directory
Leverage the power of on-premises identity and access management with Local Active Directory. Maintain control over user authentication and permissions within your organization's network.
Mobile Device Management (MDM)
Ensure the security of your mobile devices with Microsoft Intune. Centralize the management of your organization's devices, safeguarding against data breaches and ensuring compliance with security policies.
Local Exchange
Facilitate efficient email communication with Local Exchange. Manage your organization's email services locally, ensuring reliable and secure email communication within your network.

Web application & DB
Web application
1tec experts will evaluate your web application potential vulnerabilities and compromising configurations. They will also determine the security level of the database used by your web application.
DataBase
Your hosting environment will also be analyzed (Apache, MariaDB, MySQL, IIS, Tomcat, Nginx). Finally, our IT professionals will closely observe the hosting directory permissions (Linux and Windows).
Why Choose US
How do we proceed
Our experts will proceed with the security consulting using an Agile mindset. 1tec will ask customer feedback in every step of the process and will apply adjustments if needed.
INFORMATION GATHERING
Our IT professionals will deeply study your system configurations. They will gather any relevant information regarding the company use of technologies from the IT staff. Several advanced information gathering tools could be used during this step.
FULL ANALYSIS
Once the 1tec team has all the information needed, they will proceed with a full analysis. The analysis will be based of actual, relevant and known vulnerabilities and categorized by the risk of exploit level and system criticality. Some proof of concept tools and tactics might be used by the team for further analysis.
REPORT DOCUMENT
Using the data gathered and the full analysis details, 1tec will provide a complet and easy to understand report document that will allow your organization to apply the security measures needed. Our representative will give to your IT staff any further explanation needed.

A fast website
implementation
1tec is proud of its development team. Indeed, with the needed information, our web developments, designers and security engineers can conceptualize and implement a fully functional website for your organization in less than 72 hours!
Website
1tec will also efficiently transfer your developed website in a hosting and domain environment. Our security team will make sure that your website data is in the desired country, state or province because of data protection laws (Canada, Quebec, United States, United Kingdom, …).
Digital signage
Our experts will provide to your company a powerful and customized digital media solution with a cloud-based content management system (CMS) that allows content to play on many screens dynamically. Our technicians can setup a video wall, single screen and touch screen displays. The included CMS has a powerful system monitoring that has many functionalities such as screen monitoring, media player uptime and downtime monitoring, reports and a set of tools that can fix issues remotely. Digital Signage FAQ

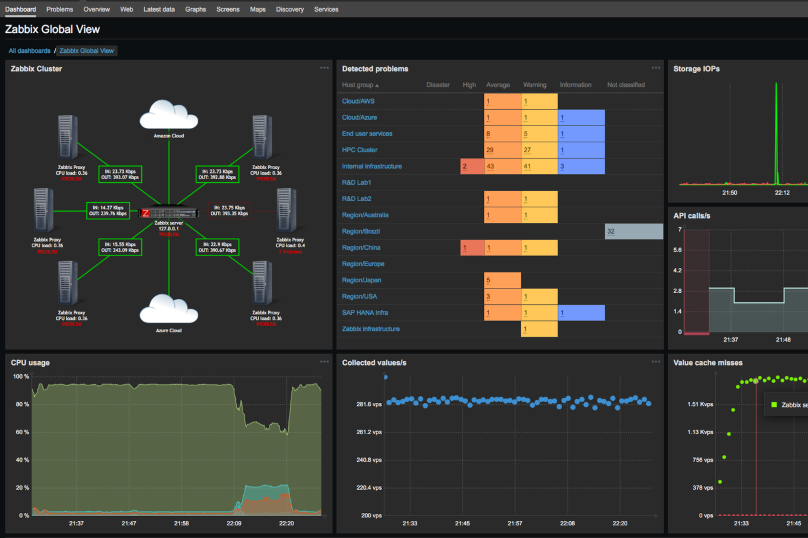
Network monitoring
1tec provide this solution to small and medium size companies. This solution will allow your company to monitor precisely network infrastructure such as routers, switches and firewalls, Windows and Linux servers and all end-user hosts in a network segment. The network monitoring solution provide various real-time content such as servers up/down state, CPU activity, network activities, OS features, VPN up/down state, ICMP ping, database state and requests and website uptime. With this solution, you can easily configure and receive real-time email and notification in case of a critical situation in the network.
A few things we’re experts of
Support: Once the website has been implemented, 1tec will support you on every step of updating information on your website using WordPress account.
SEARCH ENGINE OPTIMIZATION
Search Engine Optimization (SEO) tools, our marketing and development team will make sure that your website can be easily found on Google search by your clients.
Wordpress
1tec is able to efficiently implement a website using WordPress. We can also adapt several WordPress templates for your organization.
SECURITY
Our security team will implement several security tools and solutions in both the WordPress and hosting environment. The client to server connections will be encrypted using TLS/SSL certificate and key.
Why choose our packages
UP-TO-DATE SECURE ENVIRONMENT
In every step of the process, 1tec uses up-to-date methods and data. Which is why, after the consulting, your organization will have the means for securing the IT environment.
A PERSONALIZED AND UNIQUE ANALYSIS
1tec is proud of its analysis methods. Using an agile approach, we are able to provide a fully personalized, unique and customer approved analysis.
A REASONABLE PRICE
1tec offer a reasonable security consulting price. Our prices are based of the complexity of your environment and the work that needs to be done. We can propose a price reduction for educational organizations.

Windows Environment
A Windows environment for your enterprise
1tec offers a Windows environment solution for small and medium enterprises. We will set an Active Directory infrastructure using Windows server 2016 so that our users can efficiently use a Windows network infrastructure with PCs. With the help of Single-Sign-On technology, our users can use only a unique password to have access to the email, file sharing and remote desktop environment.
RECOMMENDATIONS
Finally, once your company has read the report document, 1tec will provide a set of solutions that would help them to secure the environment. These solutions are offered based of the final result of the security report. If needed, 1tec will customize its solutions based of the reality of our client’s IT environment.
Security Wire Free Camera Installation
Click edit button to change this text. Lorem ipsum dolor sit amet
WiFi and Network Installation
Click edit button to change this text. Lorem ipsum dolor sit amet
24/7 Availability
Click edit button to change this text. Lorem ipsum dolor sit amet

Monitoring features
Reports and alerts
Our monitoring solutions are able to generate monthly, weekly and daily reports. Customized alerts and notifications can also be setup and based on critical systems. The reports include the screenshots of the screen, uptime, downtime and many useful data that our solutions bring together. All network and system events are logged and securely stored in the logging program.
Real-time activities Remote fix issues Network auditing Alerts and reports
Free Estimation
Request A Quote
I am text block. Click edit button to change this text. Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis.